thick client application test cases|thick client security : trade A OWASP Based Checklist With 80+ Test Cases. Contribute to Hari-prasaanth/Thick-Client-Pentest-Checklist development by creating an account on GitHub. Resultado da 1 de dez. de 2015 · Jogoya, Kuala Lumpur: See 432 unbiased reviews of Jogoya, rated 3.5 of 5 on Tripadvisor and ranked #1,217 of 5,516 restaurants in Kuala Lumpur.
{plog:ftitle_list}
webRead about Pure Cuteness 3D Lolicon pack Vol.26 – Lolicon and Shotacon Hentai: 3D, videos, manga and more by viphentai.club and see the artwork, lyrics and similar artists.
Dive into the world of thick client applications! Learn about their vulnerabilities and how to conduct effective security assessments.This repository serves as a guide for understanding and addressing these challenges, covering various aspects of thick client penetration testing such as information gathering, traffic . Microsoft Outlook, Yahoo Messenger, and Skype are some thick client application examples. How to test thick client applications? 👨💻. Thick Client Pentest is complicated as compared to /API Pentest in my opinion. .A OWASP Based Checklist With 80+ Test Cases. Contribute to Hari-prasaanth/Thick-Client-Pentest-Checklist development by creating an account on GitHub.
Read on to learn about what thick client penetration testing is, its types, and how it’s carried out. Discover Breachlock’s multi-faceted approach to thick client penetration testing. Testing of a thick client application. There are three stages of thick client application testing. Dynamic Testing; System Testing; Static Testing; Dynamic testing. In this .
Thick client penetration testing is a proactive approach to evaluating and enhancing the security of applications that run locally on a user’s device.In this article, we have set up a lab to practice thick client application penetration testing and then we discussed various information gathering techniques. In the next article, we will discuss . In this series of articles, we will learn various tools and techniques used to perform thick client application penetration testing. A step by step breakdown being deployed, we will discuss about starting with the very basics . A step by step breakdown being deployed, we will discuss about starting with the very basics to the advanced test cases. Introduction . Referenced under multiple names, such as: Fat client/Heavy client/Rich .
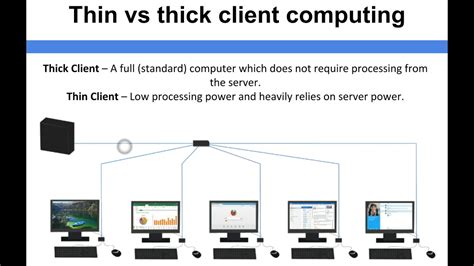
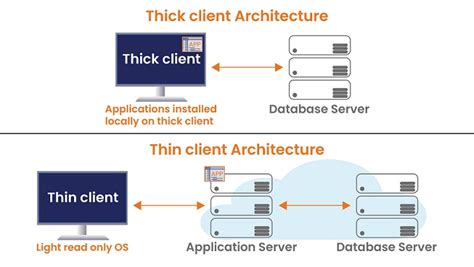
This repository aims to familiarize you with Thick Client Application security concepts, providing a comprehensive guide and practical methodology for thick client Pentesting. Whether you're a beginner or an experienced security professional, this repository will equip you with the knowledge and tools needed to effectively assess the security .Burp Suite Enterprise Edition The enterprise-enabled dynamic web vulnerability scanner. Burp Suite Professional The world's #1 web penetration testing toolkit. Burp Suite Community Edition The best manual tools to start web security .Thick Client Penetration Testing (a.k.a. Thick Client Pentest, Thick Client VAPT, Thick Client Pen Testing) identifies exploitable vulnerabilities on both the local and server-side. The attack surface is larger and requires a different approach from web application penetration testing. A thick client is a software application that has most of the resources installed locally for processing on typically a personal computer. Thick Clients follows the client-server architecture. Thick client applications are divided into two categories:
There are many test cases which aid us to perform static analysis. . Proxy-Aware Thick Client: If Thick Client application has a built-in feature to set up a proxy server, then it is known as a proxy-aware Thick Client. Brp Suite (Burp's Invisible Proxy Settings to Test a Non-Proxy-Aware Thick Client Application): Go to Request handling in .
thin client vs thick client
thick client software
Thick client applications can be developed using Java, .Net, C/C++, etc. A thick client may follow two-tier architecture or three-tier architecture. . Under network communication used in application (2) Following Test Cases need to be performed (but not limited to) Test the application for sensitive information; Test Injection vulnerabilities; Auditing Thick Client applications for vulnerabilities generally include Authentication bypasses, Unauthorized executions, Privilege Escalations and Sensitive Information disclosures through .
Vulnerable Application: Damm Vulnerable Thick Client App (DVTA) As shown in the screenshot, the path is missing. An attacker can create the folder and DLL file and escalate the privilege. SQL Injection. A SQL injection attack consists of the insertion or “injection” of a SQL query via the input data from the client to the application.
Thick client Test cases. INFORMATION GATHERING Information Gathering Find out the application architecture (two-tier or three-tier) . Try to patch the application. Test For Decryption And DE obfuscation Try to recover original source code Try to .In general, it would be safe to assume most employees will need to utilize the same, or similar, client applications and files. A thick client could come with the list of business applications needed. Because the computer has all of the hardware and software needed, the employee only needs to connect to the company's server to download updates . Do you need to automate a thick client application like WPF, Silverlight, Win32 or WinForms? If so, then White may be the automation framework for you. . We have saved 50% time in creating test cases/user scenario tests vs. Selenium and the test execution results on the CIS are very reobust. Yours, Jogi. SreeCharan Shroff says: May 12, 2016 .
Leadership | Meet the team guiding Black Duck's vision and strategy.; Newsroom | Latest news, press releases, and media coverage about Black Duck.; Blog | Insights, updates, and expert opinions on application security.; Partners | Information on Black Duck's partnerships and collaboration opportunities.; Careers | Explore job opportunities and career paths at Black Duck.Thick client applications can be categorized into two-tier and three-tier architecture. In two-tier architecture, the application is installed locally on the computer and communicates directly with the database. . In this case, the application server and the database might be located on the same network or over the internet. This is something . Conclusion. This blog highlights different tools and approaches for testing a thick client application for vulnerabilities. The tools have remained the same over a period of time and there are no major changes in the way thick .
In this article, we will discuss some miscellaneous test cases that can be used against Thick Client Applications. These test cases include Application Logging, Developer Backdoors, Unreliable Timestamps and lack of application signing. FREE role .Test for response modification: In the case of thick clients, most of the major processing/validations are carried at the client side. As a result both the request as well as response modifications play a key role in testing the thick client for vulnera- . Thick client applications are unique and testing thick clients requires patience and a . Welcome to the part 7 of Practical Thick Client Application Penetration Testing using Damn Vulnerable Thick Client App (DVTA). . In the next article, we will discuss some miscellaneous test cases that can be used against Thick Client Applications. Posted: September 23, 2016.
Thick Client Applications, commonly known as Desktop Applications, rely on client-side processing and follow a traditional client-server architecture. . Our deliverables include test cases that we run to bypass business logic vulnerabilities on each functionality that is critical to business. Request Assess. Education Material Section. A OWASP Based Checklist With 80+ Test Cases. checklist penetration-testing pentesting thin-client penetration-testing-framework . (thin Client) and Thymeleaf Rich Internet Application (thick Client) javascript mysql css java html website sql thymeleaf java-ee eclipse-ide mysql-database mysql-workbench thin-client rich-internet-application .Thick Client Application Penetration Testing Course Introduction Course Introduction (1:37) Help and Support Downloadables Introduction and Lab Setup Introduction to Thick Client Applications (4:12) Lab Setup - Part 1 (2:04) Lab Setup - Part 2 (18:44) The Pre-Course Challenge (2:32) . Selecting the method for Thick Client Pentesting. For thick client penetration testing, there are two key methods: Black-Box Testing: It is the testing approach where the testers initiate the test without any prior knowledge about the app’s configurations.They carry out the testing of all functionalities of the application without any access to design, operation, and .
The client was working at a thick client application for mobile devices. . Then we elaborated the test cases that could be automated and included in regression testing. We helped to integrate API, created and automate unit tests, functional tests, performance tests for the system.
In some cases a thick client application will respect the proxy settings of the system you are using to run Burp Suite. However, it is often the case that these clients don't support HTTP proxies, or don't provide an easy way to configure them to use one. Burp's support for invisible proxying allows . Examining traffic between a thick client application and the server can reveal sensitive, unencrypted data, such as Clear-text credentials, secrets, and API keys; We will analyze FTP traffic generated by DVTA. To do this, launch Wireshark and select “Adapter for loopback traffic capture.” . Learn the basics of how to test thick client applications, the challenges and best practices for testing, and the tools you can use to help secure your system. Toggle menu. Home; Company. . Let’s examine a couple of real-world examples that highlight the importance of thick client penetration testing: Case Study 1: Banking Application . A thin client is a computer system that runs on a server-based computing environment. They work by connecting to a remote server-based environment, where most applications and data are stored. The server performs most of the tasks like computations and calculations. They are more secure than thick client systems when it comes to security threats.
thick client security testing
wood moisture meter calibration
Placares ao vivo, jogadores, programação da temporada e resultados de hoje do Toronto FC estão disponíveis no Sofascore. Próxima partida do Toronto FC. O Toronto FC .
thick client application test cases|thick client security